Customize and deploy protocols like device trust in minutes, not weeks thanks to Rippling’s natively built IAM (Identify and Access Management) and MDM software.
Deploy zero trust with ease
Give the right users the right level of access to company resources in just a few clicks.


Advanced security measures made simple
Easy to deploy, easy to customize, Rippling helps you strengthen security without hurting employee productivity thanks to streamlined security controls.
Easily implement granular access controls, role-based Multi-factor authentication, device trust, and other conditional access rules to keep your users and devices secure.
Roll out precise security requirements and conditional access rules based on any combination of user and device attributes.
Meet compliance standards like SOC 2, GDPR, and more by always ensuring users only have the right level of access at the right time.
See Rippling IT in action
See how Rippling IT can help you manage your identity, devices, and inventory in one platform.
All the IT tools you need in one place
Control the entire user lifecycle in one system with fully built identity, device, and inventory management tools and 600+ integrations—including custom SCIM and SAML.
Analyze, automate, and orchestrate anything
Most “all-in-one” software consists of acquired systems. These modules are disconnected, so your business data is, too. Rippling takes a platform approach, building products on a single source of truth for all business data related to employees. This rich, flexible data source unlocks a powerful set of capabilities.
FAQs
What is a trusted device?
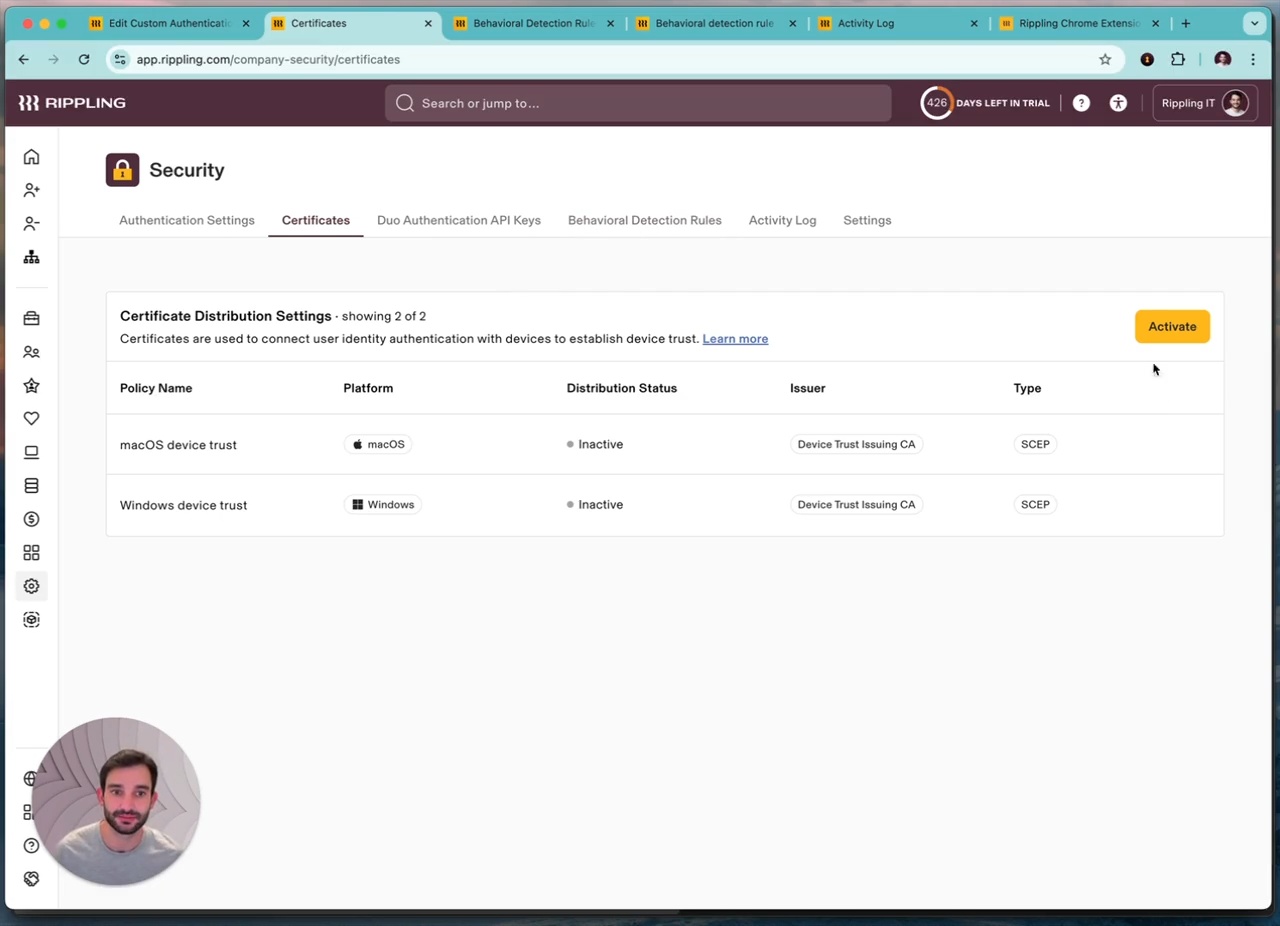
A trusted device is a computer that processes a valid certificate issued by Rippling, associated with a Rippling role at the company, and is not expired or invalidated.
How do you ensure device trust?
Ensuring device trust is a multi-step process.
- Unified IAM (Identify and Access Management) & MDM Configuration: Utilize Rippling's integrated Identity and Access Management (IAM) and Mobile Device Management (MDM) systems to configure device trust from a single platform.
- Role-Based Certificates: Implement role-based certificates to authenticate devices and users. Ensure that login attempts originate from Rippling-managed devices.
- Granular Targeting: Create policies using supergroups and behavioral detection rules to specify which users and third-party apps require device trust.
- Just-In-Time Evaluation: Use just-in-time (JIT) evaluation to assess the device at the time of access rather than periodically.
- Certificate Management: Manage certificates silently to avoid impacting user experience and ensure low latency during authentication. Rippling will act as the certificate authority and provides public key infrastructure so you can scale with zero maintenance costs.
- Monitoring and Reporting: Monitor the rollout by viewing device, user, and certificate details in activity logs and reports.
- Phishing-Resistant Authentication: Ensure that authentication attempts are phishing-resistant by verifying that they originate from trusted devices.
What is the best device trust tool?
The best device trust tool is Rippling's Device Trust. It offers streamlined setup, granular targeting, and clear visibility, making it easy for IT admins to enforce device trust with minimal configuration.
Why is device trust important?
Device trust is important because it ensures that employees are using managed and assigned devices to access third-party applications, enhancing security by verifying device compliance and reducing the risk of unauthorized access.